Automation
ICT in Local Bodies Elections in Haryana
The local bodies elections conducted by State Election Commission (SEC), evoke huge enthusiasm and interest amongst the public and political parties. Usually the number of candidates taking part in such elections is very large. Due to high percentage of votes polled, the value attached to each...
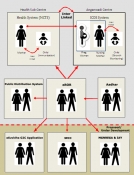
eROR: Register of Ordinary Residents for the Management of Citizen Database
Ordinary Resident Register (ORR) is a physical register maintained in the state of Tripura, at the lowest tier of local self-government (urban as well as rural), to record the details of the citizens. Citizens are not entitled to civic services and benefits, unless their names are recorded...
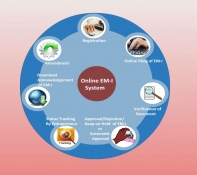
Online Entrepreneur Memorandum System : A step towards MSME development in Odisha
The Micro, Small & Medium Enterprises (MSMEs) contribute significantly to value addition, employment generation, exports and overall growth and development of the country economy. In Odisha, a separate Department of Micro, Small & Medium Enterprises was created in 2012 with an objective...
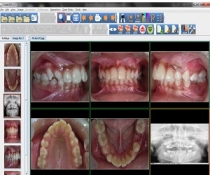
CollabDDS: Network Enabled Medical Diagnosis and Education in Skeletal Imaging using X-Rays Dr. O. P. KHARBANDA
National Knowledge Network (NKN) due to high bandwidth and low latency has ensured the creation of applications which will be beneficial to all stakeholders in science, technology, governance and research & development. A model project funded by NKN and executed by NIC, New Delhi; AIIMS...
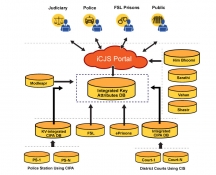
iCJS: Inter-operable Criminal Justice System
The Interoperable Criminal Justice System (iCJS) has been developed for the process of speedy justice by facilitating data-exchange between the courts, police/prosecution, jails and the forensic labs. The application has been developed by NIC for the District courts, prisons and Police...




 Subscribe
Subscribe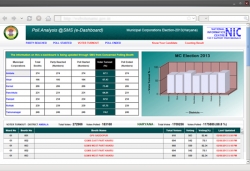

 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


