Technology
Artificial Intelligence - Growth Engine for Present & Future
Artificial Intelligence (AI) is the study and creation of computer systems that can perceive reason and act. The primary aim of AI is to produce intelligent machines. The intelligence should be exhibited by thinking, making decisions, solving problems, more importantly by learning. AI is an interdisciplinary...
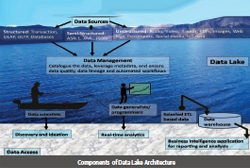
DATA LAKE - A Paradigm Shift in the Next Generation Reservoirs
Data lake typically uses low-cost commodity servers in a scale-out architecture where servers can be added as needed to increase processing power and data capacity. In comparison, data warehouse can't be scaled cost-efficiently to process the growing data volume. Data lake provides fast access to...
Land of Festivals Empowers Citizens with ICT Enabled eGovernance Services
NIC has been the pioneering in ICT activities for good governance of the State of Nagaland since 1989. While successfully implementing many citizen centric projects, services and ICT enablements in the State, NIC Nagaland advances ahead with a number of new projects and initiatives. Many of...
Sun Rise State Striding ahead with Excellence in e-Governance through ICT
Besides developing and implementing eGovernance applications and other customised software, a host of Services are offered by the NIC State Centre, Andhra Pradesh. These include Video Conferencing, Virtual Class rooms and supporting various ICT initiatives through NICSI. In addition, Data...
Lsyncd (LIVE SYNCING DAEMON)
Lsyncd is a light-weight data replication tool which is free, easy to install and convenient to configure. It is an open source technology based, ultimate host to host replication or mirroring tool with very minimal configuration, cost effective and can assure the RPO in minutes or even seconds.




 Subscribe
Subscribe




 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


