e-Services
MUZAFFARNAGAR: Treading fast on e-Governance turf
Muzaffarnagar, located in the northern part of Uttar Pradesh is popularly known as The Sugar Bowl of India. With a population of 41,38,605 (Provisional figures of the 2011 census of undivided Muzaffarnagar) the district spreads over an area of 4049 square kilometers and has 4 tehsils, 9 development...
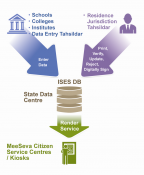
ISES- Integrated Socio-Economic Survey of Students
The Government of Andhra Pradesh has desired to deliver the citizen-centric services from a centralized location through all citizen service centres such as e- Seva, AP Online, CSCs across the state under a new initiative called MeeSeva. A web based application- ISES has been designed and developed...
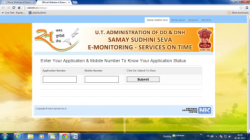
SAMAY SUDHINI SEVA- Online Monitoring of Time Bound Services
UT Administration of Daman & Diu and Dadra & Nagar Haveli in collaboration with National Informatics Centre have implemented an online web based Monitoring System for time bound services known as Samay Sudhini Seva.
LAKSHADWEEP ISLANDS- Digitally Bridging the Nautical Seclusion
The Union Territory of Lakshadweep (UTL) is geographically dispersed in the Arabian Sea with its capital at Kavaratti. It has achieved enormous success in deliverance of ICT services to its citizens despite its geographical isolation and bandwidth insufficiency, using the reliable and efficient infrastructure,...
ROHTAK: ICT Hub for e-Governance in Haryana
The district derives its name from its headquarter town Rohtak, which is said to be a correction of Rohtashgarh, named after Raja Rohtash, in whose reign the city is said to have been built.




 Subscribe
Subscribe



 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


