Articles
Cloud Computing: An Innovative Approach in IT
With every day innovations in IT world, the way IT corporations and business organization benefitting from such innovations keeps growing. Cloud computing is a major shifting in the way IT organs in the organizations worldwide is going to look like and perform in the near future. It has already become...
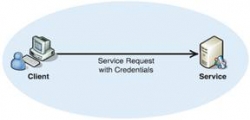
Service Oriented Architecture: In the Security Perspective
As electricity, if used tactfully then many useful things can be done but a little carelessness can make a big loss. As the same way Information, if accessed by the authorized person, produces effective output but unauthorized access to the same may create unpredictable nuisance. Many e-Governance...
ICT Initiatives in HP Police
Sh. G S Gill, IPS & Director General, Himachal Pradesh Police speaks to Informatics on the various e-Governance Initiatives undertaken successfully in the HP Police Department.
Haryana :Spearheading the e-Governance Initiatives
Haryana State is one of the most progressive states of the Indian union with total geographical area (44212 Sq. Km) of only 1.4% of the country geographical area. A leading food grain producer, it is also one of the states with very high per capita income. The Software & IT/ITES/BPO services exports...
KERALA: ICT in the land of Backwaters
Kerala "Gods Own Country", is the first Indian State to achieve total literacy. NIC Kerala was established in 1987 as part of nationwide computer and communication network, NICNET. NIC district centers are located in the 14 district head quarters attached to the collectorate.




 Subscribe
Subscribe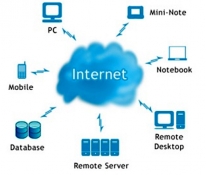




 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


