Articles
OCMMS for State Pollution Control Board
Online Consent Management & Monitoring System for State Pollution Control Board (OCMMS) is web based Generic Model for implementing a well-coordinated system applicable to most SPCBs and PCCs. This system allows industries for the online submission of application for CTE/CTO & for various categories...
Web Ratna Awards
e-Governance has received a tremendous boost in India and that gave National Informatics Centre, the inspiration to institute the Web Ratna Awards, an initiative to acknowledge the exemplary initiatives in e-Governance using the medium of World Wide Web.
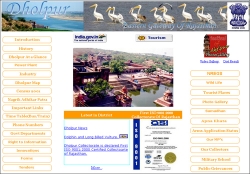
Dholpur: ICT Shines on the Eastern Gateway of Rajasthan
Situated in the eastern part of Rajasthan bordering Uttar Pradesh and Madhya Pradesh, Dholpur earlier called Dhavalpur, was carved out of Bharatpur in 1982. It is famous for its sandstone and ravines which are part of Chambal legacy. The famous Dholpur House (UPSC HQ), President House and...
Imphal East: e-Governance Deep Rooted with Land Records & CICs
With the computerization of "Land Records" i.e. Loucha Pathap, covering sixty five villages, and the establishment of Community Information Centres (CICs), the district stands apart from others. The computerization effort by the district administration in association with NIC in...
Amravati: Using ICT to Reach the Poor Directly
Amravati is also known as Amrawati or Amraoti. It is believed to be the city of Lord Indra, the king of gods. The city boasts of historical temples of goddess Amba, Lord Shri Krishna and Shri Venkateshwara. But today the district is known for its robust ICT implementations, advanced communication technologies...




 Subscribe
Subscribe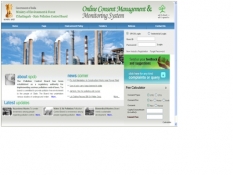



 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


