News
Honble Chief Minister, Assam, reviews KRITAGYATA (Online Pension Sanction and Payment Tracking)
On 26th June 2021, Dr. Himanta Biswa Sarma, Hon’ble Chief Minister of Assam reviewed the activities of Pension & Public Grievances Department, Assam. During the review, Hon’ble Chief Minister also reviewed NIC developed portal “Kritagyata”, an online pension sanction...
Chhattisgarh to have unique Identification of Land parcels. Revenue Secretary Launches ULPIN
On 23rd June 2021, Ms. Reeta Shandilya, Secretary, Revenue & Disaster Management, Govt. of Chhattisgarh launched the ULPIN (Unique Land Parcel Identification Number) utility for Chhattisgarh in the virtual presence of Shri Ajay Tirkey, Secretary, DoLR, Govt. of India, Shri Hukum Singh Meena, Addl....
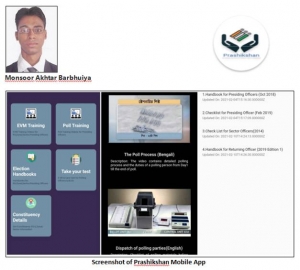
Prashikshan Mobile App - An initiative by District Election Officer Hailakandi
The app will be a ready reckoner for the polling personnel who have undergone training for the upcoming Assembly election to three legislative constituencies of Hailakandi, Katlicherra and Algapur slated for April 1, 2021.The detail poll process from Day 1 till the end of the exercise will be available...
Smart card DL/RC to be delivered at the door step by speed post. Chhattisgarh becomes first implementing state of Vahan & Sarathi faceless services
The Chhattisgarh Transport Department is going to deliver the Smart Card based Driving License (DL)and Registration Certificate (RC) to the citizens of Chhattisgarh at the address registered by them on the Transport portal. On 1st June 2021 Hon’ble Chief Minister of Chhattisarh, ...
Remembering Dr. N. Seshagiri, India's ICT Evangelist and Founder Director General of National Informatics Centre
Dr. Narasimaiah Seshagiri, Padma Bhushan Awardee and a pioneer of revolutionary changes in the technology domains of space, satellite communication, electronics, and public private partnerships in e-Governance left for heavenly abode on 26th May, 2013. Eight years have passed by, but his futuristic...

 Subscribe
Subscribe



 Flipbook
Flipbook PDF (6.8 MB)
PDF (6.8 MB)



