Technology
WEB PAGES WITH RAZOR SCRIPTING NEW VIEW ENGINE IN ASP.NET
Razor syntax is based on technology from Microsoft called ASP.NET, which in turn is based on Microsoft .NET Framework. The Razor syntax gives you all power of ASP.NET, but using a simplified syntax that's easier to learn and it can be used with existing ASP.NET Web Site.
TRANSACTION TERMINALS IN E-GOVERNANCE
Transaction Terminal is a mobile handheld data terminal which has the ability to capture, process and transmit information to host computers in real time. New models of handheld devices come with seamless connectivity options like GSM/GPRS, CDMA and Ethernet. Also, they support all the payment related...
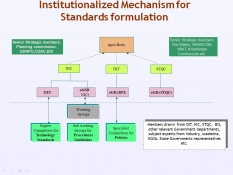
Standards for e-Governance
The Government of India has launched the National e-Governance Plan (NeGP) with the intent to support the growth of e-Governance within the country. While the e-Governance initiatives are being taken by various sectors, the same information from an individual is asked for repeatedly in different formats,...
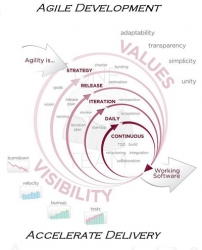
Agile development model for E-Governance Software
Agile methods typically involve a test driven approach to development, and more and early testing leads to greater quality. Amongst a few well established agile development models are Agile modeling, Agile unified Process (AUP), Extreme Programming, Scrum, and Feature Driven Development.
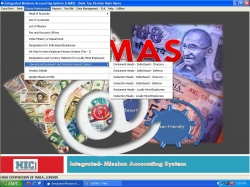
Integrated Missions Accounting System
Right now every activity of accounts sections in the missions is fully computerised through I-MAS. However it was prior to I-MAS era that missions were using the manual or semi-automatic procedures. In fact through I-MAS we have tried to cater the very complex accounting procedure of the missions in...




 Subscribe
Subscribe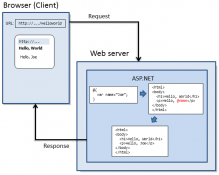


 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


