Technology
NextGen DISE NextGen District Information System for Elections
NextGen DISE developed by NIC Punjab comprises of Polling Personnel Management System (PPMS), Poll Activity Monitoring System (PAMS) and Queue Information System (QIS). PPMS is a web-based software for data digitization, data import and random deployment of Polling Staff,...
PM Poshan Shakti Nirman Portal Enhancing Efficiency and Transparency in School Nutrition Programs
MP State PM Poshan Shakti Nirman Portal enhances the Pradhan Mantri Poshan Shakti Nirman scheme by automating food grain provisioning, ensuring transparency with Aadhaar-enabled authentication, and facilitating timely digital payments. This digital platform streamlines operations to deliver...
UEBA An In-depth Exploration of User and Entity Behavior Analytics
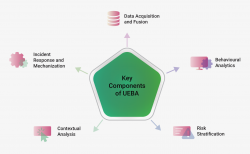
UEBA revolutionises cybersecurity by scrutinising the behaviour of users and entities within a network. Through advanced analytics and machine learning, UEBA identifies anomalies in real time, allowing organisations to detect potential security threats swiftly. By establishing baselines of normal behaviour...
West Bengal State ICT towards good governance, reaching the unreached
NIC West Bengal stands as a cornerstone in technological innovation and digital transformation, driving impactful initiatives to empower government departments and citizens alike. It serves as a catalyst for modernizing governance by providing robust IT infrastructure, innovative solutions, and technical...
AQCMS Revolutionising Agricultural Quality Control
AQCMS, developed by NIC, Central Projects, Nagpur, redefines AGMARK certification by replacing manual procedures with a robust digital platform. Built on Certification Management, Laboratory Management, and Content Management System (CMS) modules, AQCMS streamlines compliance and laboratory...




 Subscribe
Subscribe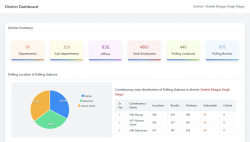




 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


