News
Honorable Chief Minister of Haryana inaugurates Online Donations System for Mata Mansa Devi Temple, Panchkula
Mansa Devi temple is one of the oldest shrines of northern India in the foothills of the Shivalik range and is an epitome of the age old tradition of Shakti worship in the region. The board has also started receiving donations from devotees living in abroad. On the first Navratra, Honorable Chief...
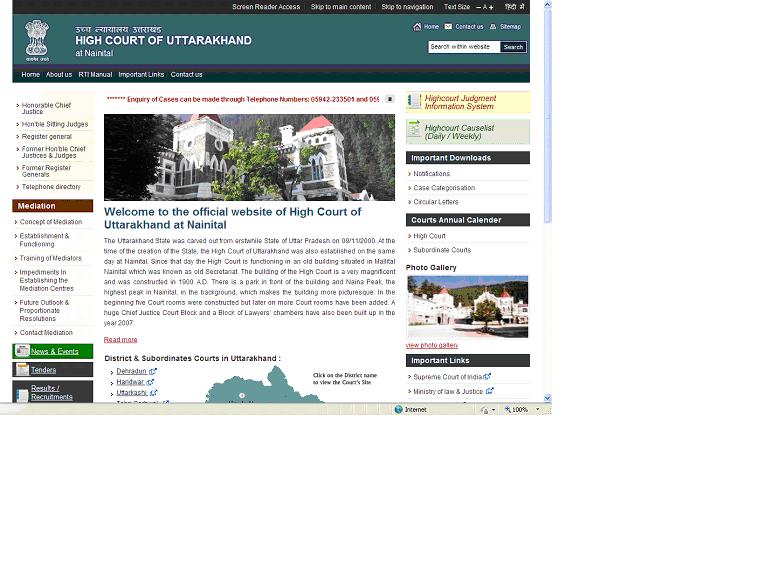
Inauguration of Websites of Highcourt of Uttarakhand and all the 13 District Courts in the state by Hon. Chief Justice of Uttarakhand
Hon.Chief Justice of High Court of Uttarakhand, Mr.Barin Ghosh inaugurated the websites of “High Court of Uttarakhand” and “all the 13 subordinate District Courts in the state” on 16th Mar-2010 at High Court, Nainital in the presence of all the Hon. Judges, Registrar General...
Video Conference facility inaugurated at State Information Commission, Punjab
State Information Commission is now connected with all the districts of Punjab through NICNET. To provide the citizens a better service and easy reachablity State Information commission has established Video Conferencing facility in its...
Workshop on e Granthalaya held at Ranchi (Jharkhand)
A workshop on e Granthalaya software was held at Birsa Institute of Technology - Trust (BITT), Getlatu, Ranchi from 22nd to 24th Feb. 2011. Shri Shahid Ahmad, SIO inaugurated the workshop along with Prof.(Dr.) Sudama Choubey, Director, BITT. Speaking after inaugurating the workshop,...
Refresher Training For NIC Officials
Refresher Training For NIC Officials A five day maiden refresher training programme on "Technological Aspects" of various NIC projects was organised at NIC Hanumangarh Rajasthan from 31st Jan. - 4th Feb.2011. Vishwanath Sharma, DIO, Hanumangarh & PSA informed that...




 Subscribe
Subscribe




 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


