Automation
eSpecial Road Tax Payment System:Simplifying Route Permit Issuance and SRT Payment
eSRT has immensely simplified the entire process of paying the monthly Special Road Tax for commercial vehicles in the state of Himachal Pradesh. With the entire process online the vehicle owners can make their payments directly from their smartphones.
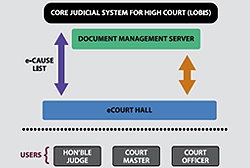
First Paperless Court of Judicature at Hyderabad
The software can also record the dictation of the judgment into the computer which can be subsequently used by the Stenographer for transcription.
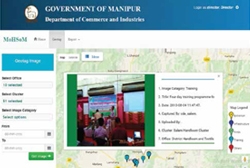
Monitoring of Handloom Schemes of Manipur using GIS
GIS based applications are being used widely for analyzing and providing decision support for various activities. MOHSOM Software uses the technology to track the events and activities of the handloom schemes being implemented in a Cluster and thereby provide support in decision-making to the State Department
Telangana's Rashtriya Bal Swasthya Karyakram Software
This software captures various health conditions of children in the target age group. In cases where diseases are detected, or if medical intervention is required, support is provided free of cost and the parents of the affected children are informed through SMS automatically.
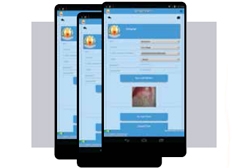
Oral Pre-Cancer Mobile App
The innovative App is very useful for Doctors and Dental Assistants in the diagnosis process and management of oral cancer in its early stages. ICT thus helps improve the quality of life of the citizens and saving lives using the best that ICT has to offer.




 Subscribe
Subscribe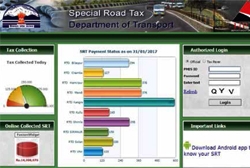


 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


