Digitization
Building Secure Applications Cybersecurity Best Practices for Modern Architecture
Applications expose resources to targeted users and potential attackers. A secured architecture is the foundation of any application defence against cyber threats. It provides a proactive and strategic defence, anticipating and mitigating potential risks before they manifest. It ensures a robust...
Jammu and Kashmir Jammu Heritage, Kashmir Splendor: Driven by Technology
Jammu and Kashmir, India northernmost Union Territory, blends cultural richness with technological progress. Since its restructuring in 2019, NIC J&K UT Centre has driven digital transformation, offering over 330 e-Services across key sectors like healthcare and educa- tion. Milestones include...
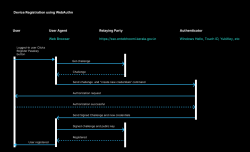
Passkeys and WebAuthn Revolutionizing Authentication with the Passwordless Technology
Passkeys and WebAuthn are revolutionizing digital authentication by eliminating passwords and enhancing security. WebAuthn, a FIDO2 standard, uses pub- lic key cryptography for secure authentication, storing private keys on devices and preventing phishing and credential theft. In Kerala Entebhoomi...
Generative AI
Generative AI is experiencing unprecedented growth and adoption across diverse industries, fundamentally transforming organizational operations and the landscape of creativity and innovation. This technology, rooted in advanced machine learning algorithms, leverages vast datasets to autonomously generate...
e-Urvarak A Comprehensive Digital Governance Solution
e-Urvarak represents an advancement in supply chain governance and subsidy claim processing in the country. Boasting a user base exceeding 3.5 lakh (Govt. and Private) and facilitating transactions for more than 12 crore fertilizer buyers nationwide, e-Urvarak has emerged as a cornerstone of efficiency...




 Subscribe
Subscribe




 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


