Articles
eAwas Software & App of Chandigarh
eAwas, which aims at bringing transparency and enabling hassle free allotment of Government Houses, is a step towards taking Chandigarh into the Digital Age and using technology to solve real world problems. The portal (http://eawas.chd.gov.in) enables online submission of applications by employees and...
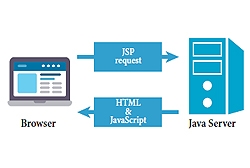
Java Help System
The JavaHelp System allows users to access the help files and topics for the CollabCAD software from their desktop or their browser application without necessarily having to install the CollabCAD software. It allows for easy access to help for beginning users and a quick reference guide for the more...
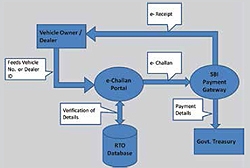
ePayment Services in Goa
With the Government of India taking steps to promote online and digital payments, the migration of the services to the ePayment channel represents major strides towards achieving decreased dependence on cash. The initiative by Transport Department, Government of Goa to allow citizens to pay the various...
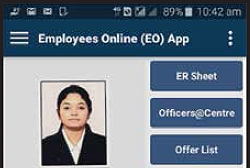
Employee Online App
In near future, the 'Push Notification' service of EO App will be decoupled and provided as a component or a web service so that it can be resused by other applications.
ServicePlus
A versatile application that allows Government officials and departments to quickly and easily create, format, publish forms, notifications etc., ServicePlus has a simple drag and drop functionality, in addition to many other advanced features, which makes it unique.




 Subscribe
Subscribe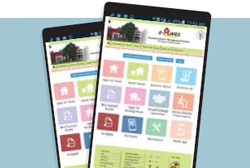


 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


