Articles
ON-LINE WEB COUNSELING
State Council of Higher Education (APSCHE), Department of Technical Education (DTE) of Government of Andhra Pradesh and National Informatics Center (NIC),Govt. of India together evolved a new system for students' admission into various technical courses in various colleges across the state, through...
CENTRALISED ONLINE STATE GOVERNMENTS EMPLOYEES COMPLAINTS MONITORING SYSTEM
A Centralized Online State Governments Employees Complaints Monitoring System has been developed by NIC for transforming conventional existing System into more efficient and transparent system. The System has also been customized so as to have the central database server at CAG office and the software...
e-OFFICE: DIGITAL SIGNING TOOL FOR SECURE DOCUMENTS
Automation has become an integral part any organization through information digitalization leaving away the manual process using physical paper documents. Instead of routing the paper documents manually, the electronic channels have been used extensively for transitioning the documents in digital form....
WORK FLOW BASED REGISTRATION OF DOCUMENTS IN MANIPUR
Registration system in Manipur encompasses registration of documents involving changes in ownership and transactions for immovable properties as well as marriage registration with the authority concerned. This system ensures and guarantees legal ownership of title to the party.
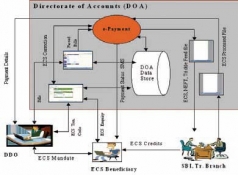
GREEN INITIATIVE BY GOVERNMENT OF GOA: e-PAYMENT SERVICES
NIC, Goa has incorporated e-Payment services by developing a web based interface to be used by all the DDOs/Departments in the existing system at the Directorate of Accounts. e-Payment Services are executed with the help of State Bank of India (SBI, Treasury Branch) Panjim branch.




 Subscribe
Subscribe



 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


