Technology
WEB APPLICATION FIREWALL -Defense against Layer-7 Attacks
The application layer (L7) is the hardest to defend. Hackers get direct access to the bounty they are seeking, by compromising layer-7. The need is to have a product with an understanding of the real-world techniques or methods hackers use. It is here that the Web Application Firewall...
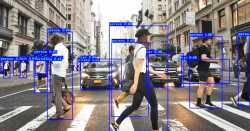
Object Detection Technologies - A simplified explanation of YOLO class of algorithms
It is of the highest importance in the art of detection to be able to recognise out of a number of facts which are incidental and which are vital
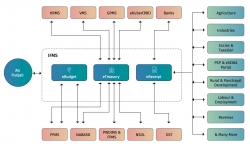
IFMS Punjab - The Next Gen Integrated Financial Management System
With release of Revised Estimate (RE) for Financial Year 2020- 21, Government of Punjab has shifted to next-gen Integrated Financial Management System (IFMS) developed by NIC Punjab. In addition to usual features of an IFMS like planning, budgeting, receipt, expenditure, bill and payment...
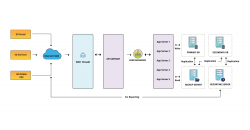
Integrated ShalaDarpan - Decision Support System for Schools Monitoring & Management
ShalaDarpan is a unique idea to provide an end-to-end solution to the Education department for effective monitoring and management of all Government Schools. System facilitates decision support, Planning (School Open/ Upgrade/ Merge/ Close), School operations (Admissions, Promotions,...
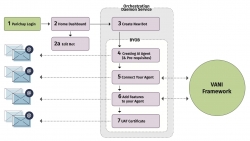
BYOB- Build Your Own Bot - BYOB + VANI = Single window destination for Bot lifecycle
As was mentioned by multiple speakers in RAISE2020, BYOB aims to democratize AI beyond the realms of technical personnel. BYOB aims to empower change-makers in the government domain like Mr. Ranjitsinh Disale (Global Teacher Award Winner 2020), a simple school teacher, who used technology...




 Subscribe
Subscribe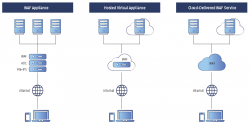

 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


