Elections
Haryana: E-Dashboard for Municipal Corporations Election 2013 (Web based Portal for poll day integrated with mobile based SMS services)
NIC-Haryana team developed a web based application for the Municpal Corporations Election-2013 held in seven numbers of Municpal Corporations of Haryana in the month of June'2013. Web based application was developed by the NIC-District Unit, Hisar and hosted at NIC-Haryana State Center under...
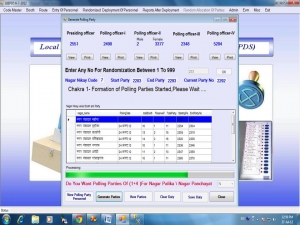
Election Personnel Deployment System for Urban Local Bodies Election, Uttar Pradesh
Uttar Pradesh is one of the largest states of the country and holding elections of Urban Local Bodies (ULB) in the state is a mammoth task with 728 seats (12 Nagar Nigam, 194 Nagar Palika & 422 Nagar Panchayat) in contention, around 35000 polling stations/booths and little more than 3 crore voters....
ICT support of NIC, Uttar Pradesh in election of Urban Local Bodies.
After 73rd and 74th Constitutional Amendments, the responsibility of conducting free & fair elections of Panchayats and Urban Local Bodies in the state has been vested in the State Election Commission under article 243K & 243ZA of the constitution of India. In Uttar Pradesh the State Election...
First Time experimented in the Elections Process - Successful Live Web Casting of Polling from 04 booths during Assembly bye-elections of Ratia & Adampur
On the directions of Election Commission of India / CEO Haryana, the district Administration of Hisar and Fatehabad were asked to make arrangements for live Web casting from 02 polling booths each from 47-Adampur (District Hisar ) & 41-Ratia (District Fatehabad) Assembly Constituencies...
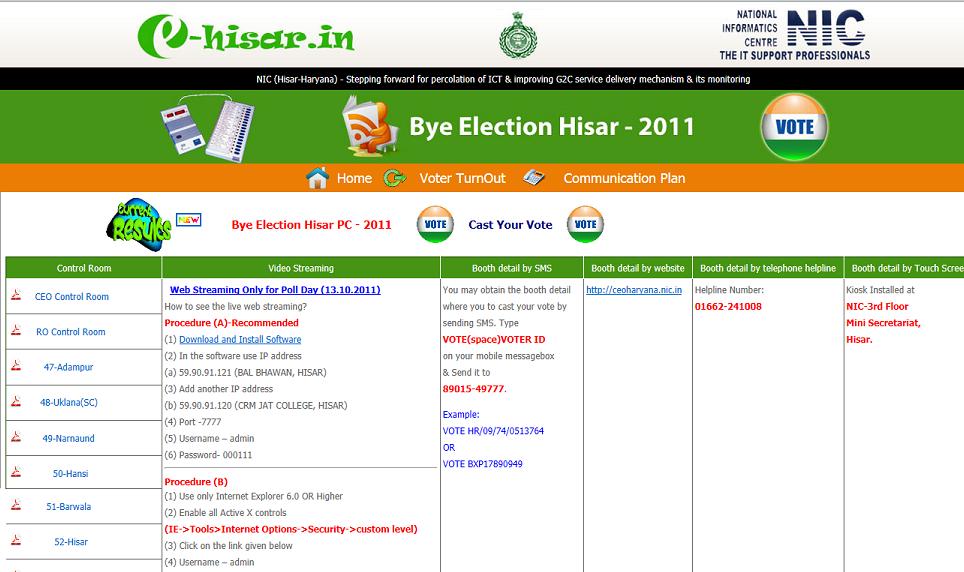
ICT support extended by NIC-Hisar during the conduction of Bye-Election 2011 (4- Hisar Parliamentary Constituency)
NIC-District Unit, Hisar was entrusted with the responsibility of computerization of various processes as mandatory part to conduct the Bye-Election-2011 (04-Hisar Parliamentary Constituency). NIC-Hisar extended not only the restless support to the District Administration but also innovated and added...




 Subscribe
Subscribe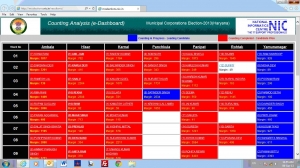

 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


