Cyber Governance
DC*Suite - Goa's Online Land Conversion Cases System
With the implementation of DC*Suite at South Goa Collectorate and related offices, physical movement of documents between stakeholders has been eliminated. The system has reduced time lags to a large extend and increased the efficiency at individual, organizational and interorganizational levels.
ICT Shines in the Sun City
Jodhpur Development Authority (JDA) was established with the objective of providing basic infrastructure in Jodhpur district to meet the ever- growing demand of public and carry out continuous improvement in the city. NIC Jodhpur Centre is providing remarkable ICT support and services to the Authority...
District Sirmaur - Committed Towards Digital India
Winning the top award during the Digital India Week celebration 2015 underlines NIC Sirmaur's true commitment towards making the dream of Hon'ble Prime Minister to transform India into a digitally empowered society and knowledge economy.
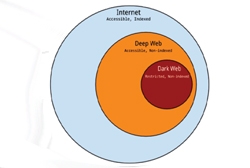
Dark Net - The Hidden Side Of Web
Dark Net is a specific part of the hidden Web where one can operate in total anonymity. It isn't illegal to browse the dark web in most countries, but using some of the dark web services can be illegal. Access of dark web is a little like stepping back in time to the early days of the internet...
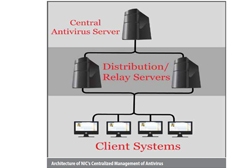
Centralized Antivirus Management
In order to have a centrally managed antivirus solution for NICNET, National Informatics Centre has deployed three-tier architecture for Antivirus management. One Antivirus Distribution/ Relay Server is deployed at each Bhawan/State and a Central Antivirus Server is installed at NIC (HQ).




 Subscribe
Subscribe



 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


