Articles
TejasVI Empowering Data Driven Governance
TejasVI transforms data analysis / visualisation for eGovernance through its user-centric design, integrating various data sources, and offering a wide range of visualisations. Notably, its features like predictive analytics, Dashboard Data Question Answering, multilingual dashboards enhance the value...
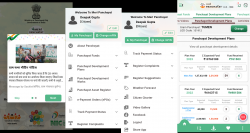
Meri Panchayat m-Governance Platform for Panchayats
Meri Panchayat mobile app aims to create a unified mobile governance platform for rural areas, including residents, functionaries, and Panchayati Raj Institution System stakeholders. It seeks to streamline and consolidate various functions and information scattered across different portals into one cohesive...
StarBus* Integrated Bus Services and Booking Portal
StarBus* streamlines and enhances bus ticketing services across State Transport Corporations/ Departments. This comprehensive platform seamlessly manages the complete ticket life cycle, offering a wide array of functionalities. From initial search and booking to secure payment processing, effortless...
eSampada Paving the Way for Transparent Government Housing
eSamapada is a digital platform ffering seamless access to data with controlled permissions for transparency. It eliminates the need for physical presence, reducing travel costs, and simplifies tasks like waitlist generation and rent assessment. This online system enhances citizen experience, saves official...
Ranchi, Jharkhand Pioneering ICT and e-Governance for a Digital Jharkhand
NIC Ranchi has championed the emerging technologies, successfully implementing various projects for all three: Central Government, State Government, and District Administration. Notable achievements include integration of VR Smart Class, development of m-Karmik mobile app, and implementation of District...




 Subscribe
Subscribe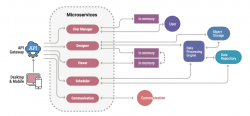




 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


