Articles
e-Panchayat Sabha A digital workplace for Gram-Panchayat Meeting
e-Panchayat Sabha is a digital workflow-based meeting process which facilitates strengthening the process of conducting meetings at the Gram Panchayat (GP) level by providing a digital interface. The application ensures better governance through effective monitoring and implementation of development...
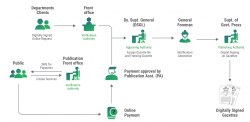
COMPOSE Comprehensive Operations and Management of Presses Over Secure Environment
COMPOSE marks a significant leap forward in Gazette Publishing, replacing age-old manual practices with a cutting-edge digital platform. This innovative solution modernizes and streamlines the Gazette Publishing process, catering to both daily and weekly Gazettes, and notably enhancing efficiency within...
Udaipur Rajasthan Empowering communities through technology for transparent, efficient governance
NIC Udaipur drives digital governance through online services, website development, software solutions, networking infrastructure, training, technical support, and data management. Collaborating with stakeholders, we identify ICT needs, develop solutions, and promote digital inclusion and innovation...
Palakkad Kerala Empowering Palakkad: Innovating for a Digital Future
NIC Palakkad has played a pivotal role in transforming e-Governance and IT infrastructure in the region. Key achievements include developing systems forland record digitization and management, enhancing survey and land records processes, and implementing a unified land management platform. Additionally,...
Darbhanga Bihar Shaping Darbhanga Digital Destiny
NIC Darbhanga excels in ICT innovation, notably implementing the e-Office system and Medhasoft for efficient governance and education management. Its high-speed VC facility was crucial during COVID-19, and its support in events like JANSAMVAAD showcases its pivotal role in digitalizing district administration...




 Subscribe
Subscribe




 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


