Ministry of Development of North Eastern Region (MDONER)
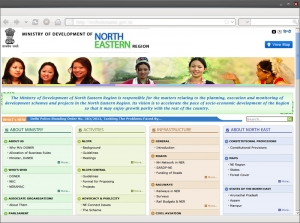
The Ministry of Development of North Eastern Region (MDONER) is accountable for handling the matters relating to the planning, execution and monitoring of development schemes and projects in the North Eastern Region of India. The aim of the website is to provide instant information about North East Region of India, various development activities in the region, Infrastructure updates, etc.
The indigenously designed website comes with a clean interface and well-laid content arranged in four broad categories on the Homepage- About Ministry (Who’s Who, Associate Organizations, Parliament, Citizen’s Charter etc.), Activities(NLCPR, Externally Aided Projects, Look East Policy, etc.), Infrastructure (General, Roads, Railways, Power, etc.) and About North-East(Constitutional Provisions, Maps, States of the North-East etc.). Photo Gallery module is incorporated for presenting the images on the website in a well-structured manner. Visitors can also do free text search in web pages as well as linked documents. Links to NLCPR MIS, File Tracking and Intranet Portal have also been provided.
MDONER website is bilingual with English and Hindi versions. The website also has explicitly stated Accessibility Statement, Compatibility Statement, Terms & Conditions, Website Policies, Copyright Policies and Disclaimer. The site comes with assistive technologies such as Screen Readers Access to facilitate readers with visual impairment.
The website has a dynamic sitemap covering links up to the last level. In terms of interactivity, the site offers links to the twitter account.




 Subscribe
Subscribe
 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


