Ministry of Panchayati Raj
The Ministry of Panchayati Raj was created as a separate Ministry on 27th May 2004. It has the primary objective of implementation of Part IX of the Constitution, Panchayats in Fifth Schedule Areas and District Planning Committees. Since under the scheme of things in the Constitution, most of the actions including framing of laws rests with the State Government, the Ministry strives to reach its goals primarily through advocacy, and also through financial support.
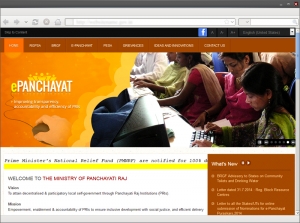
The vibrant website of the Ministry also offers rich content. The header region of the site contains information related to Rajiv Gandhi Panchayat Sashaktikaran Abhiyan (RGPSA), Panchayat Extension to Scheduled Areas (PESA), Backward Region Grant Fund (BRGF), E-Panchayat, Ideas and Innovations, Grievances and Contact Us. The important images are transitioned through an image slider on the homepage. The right hand corner of the homepage is dedicated to What’s New section. The footer region of the site contains information related to Panchayat and CSS, Areas outside Part IX, Publications & Reports, International Cooperation, Action Research, Tenders, Panchayat Finances, Gender Responsiveness, RTI, Website Policies, Help and related links.
A detailed Site Map and Search button ensures quick and smooth navigation between pages. The website has a dedicated section for inviting ideas and innovations. A link to Facebook page has also been provided. The site is compatible with all major browsers.




 Subscribe
Subscribe
 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


