Digitization
District Chamba, Himachal Pradesh
The IT revolution in Chamba kick started with the establishment of NIC District Centre in the year 1988 aiming at providing IT Support and Services to various Government and Public sector Departments. Since then, ICT has played a pivotal role in improving e-Governance and delivery of citizen centric...
HP Telestroke Mobile App
The HP Telestroke, Android based Mobile App, developed for the citizens, 108 Ambulance personnel and Doctors is proving a boon to the Stroke patients in the State saving lives and educating the masses about the action to be taken in case of such a stroke.
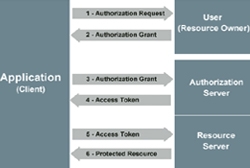
oAuth Based Single Sign-On
Introduction of oAuth 2.0 based Single Sign-On authentication mechanism in MyGov has enabled better user experience while accessing its various sites and Apps.
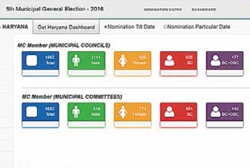
E-Dashboard for Elections
e-Dashboard is a web based online application which was launched by Haryana during the 5th general election for Municipalities of ULBs. Developed and successfully implemented by NIC Haryana, this application enhances transparency in the entire election process and has evolved to be used as an integral...
Mobile Governance In Bihar
Apna Patna App, ePACS, Digital State Assets Register, Apps for ePlantation, eNursery and Civic Amenities are some of the key mobile based solutions developed by NIC Bihar for enabling smarter eGovernance Services for the citizens of Bihar.




 Subscribe
Subscribe


 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


