Mobile based Waste Bin Clearance Monitoring System

A Mobile based Waste Bin Clearance Monitoring System was launched by Honorable Mayor of Chennai Corporation on 05/11/2013. Android based Mobiles loaded with the Application were distributed to 200 Conservancy Inspectors during the launch.
The Application has been developed for Corporation of Chennai by NIC, Tamil Nadu State Centre to Monitor the timely clearance of Waste Bins in Chennai Corporation Area. There are 15 Zones, 200 wards and 29864 streets in the Corporation. Every street has been provided with Waste Bins (Group or Single) and each Bin is given a unique Number. The Geo Location(Latitude and Longitude) along with photo of all the Bins are captured using Android based phones and stored in the Central Server of Chennai Corporation through web services.
The Conservancy Inspectors are provided with user id and password. They are linked to a Ward of a Zone in backend Application developed by Chennai Corporation. When they successfully logon to server from Mobile, all the localities and streets along with bin numbers are downloaded to their Mobile based on their User-id.
This mobile application has the facility to take the photograph of the Waste Bin along with the Geo-coordinates of the location from where the photo is taken and the time-stamp. The Inspector can upload this photograph immediately to the central server maintained by the Chennai Corporation.
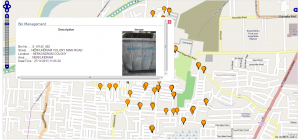
A GIS based interface developed by NIC, Tamil Nadu State Centre facilitates the senior officials of Chennai Corporation in viewing the Bins on the Open Street MAP with different color coding to know the status of the bins on a particular day. Green color on the location of the Bin indicates the Garbage cleared status, Orange color indicates uncleared status and Red color indicates non-visiting of Conservancy Inspectors to the Bin location on that day.
A Separate mobile application would shortly be released to citizens which can be downloaded by them to their Mobile. The Mobile Application can be used by citizens to capture the photograph of any uncleared bin and upload it to the server through web services in Corporation of Chennai Servers.
These complaints are monitored by designated officials for followup action.




 Subscribe
Subscribe
 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


