U.P. Commercial Tax Information Ticker : A Tool for Effective Management
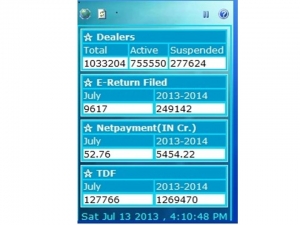
You must have heard the proverb “A stitch in time saves nine”. However, in this era of Information revolution, we need to collaborate the management cliche with the philosophy to say “Instant Information to Enhance Governance”. This precisely has been witnessed that information reaching to the top management helps entire decision making process and thereby enhances the human efforts. Information ticker, designed for the Department of Commercial Taxes in Uttar Pradesh exactly does the same job accurately and efficiently.
Developed by the NIC, “Information Ticker” has become a handy tool in the hand of the Commercial Tax Department to expand the ICT innovation in altogether a new realm, while extending the footprint of computerized, error-free and transparent mechanism. “Information Ticker” brings all the latest developments right on the computer screen of the supervisors. Indisputably, the ticker has enhanced the entire monitoring system of the Commercial Taxes Department, which supervises the entire process of dealers’ registration, online payment, E-return filing, and transit pass issuance etc.
It has been long envisaged by the Utter Pradesh government to design and develop new definitions of IT innovation in the state. Resultantly, Department of Commercial Taxes came with the user-friendly solution, which is not only useful for the end-user but the top management of the department to bring all the activities under the IT realm.
The highlight of this sidebar gadget resides in its effectiveness and precision, which enables tax officials to monitor all the critical information round-the-clock. The widget is having an option of update interval, which ensures periodical updates with fresh information at the scheduled interval. Sidebar gadgets were introduced in Windows Vista, and the gadgets are docked within the sidebar area. In Windows 7, the docking within the sidebar was removed, and the gadgets are set free to float anywhere and can be placed as per the user’s comfort. Its easy and effective.
For further details you may contact :
Mr. Sanjay Chatterjee, PSA
NIC, U.P State Unit, Lucknow
0522-2298846, sanjay.chatterjee@nic.in




 Subscribe
Subscribe
 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


