Jan Suvidha Kendra - A new hope for Pilibhit, Uttar Pradesh.

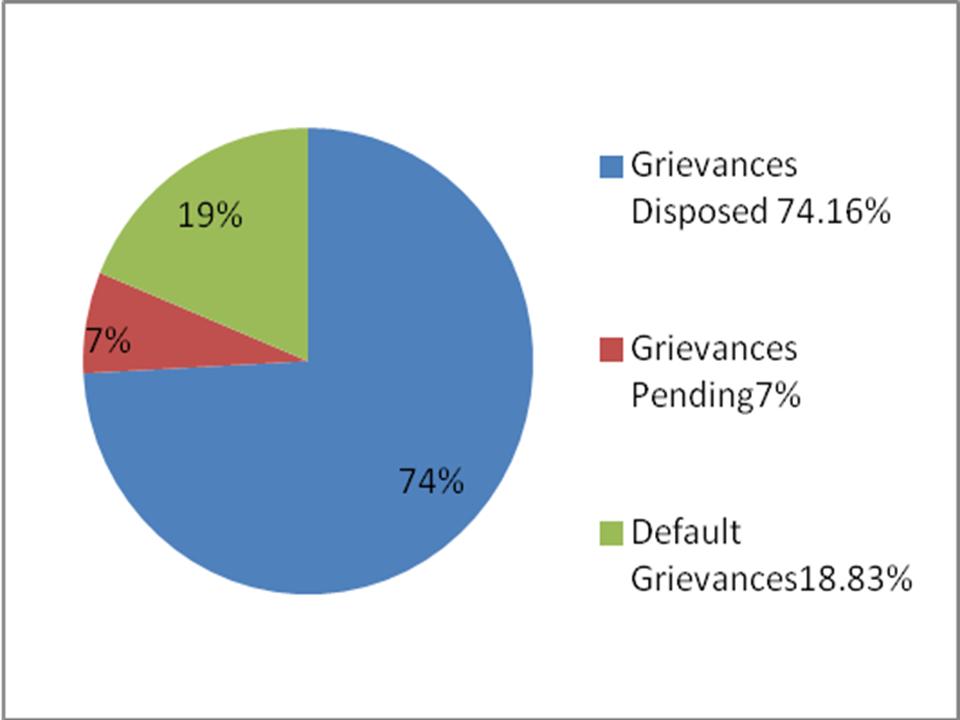
The most awaited Jan Suvidha Kendra of Pilibhit has now marked its existence in the web world with URL address www.jskpilibhit.com. It was inaugurated by commissioner of Bareilly Sri K. Ram Mohan Rao as on 22nd May 2012. JSK offers a unique way to address public grievances. It records the public grievances and passes it to the concerned government department for immediate action. A complainant just needs to have an access to telephone for getting the grievance recorded. For registering grievances, specific phone numbers are publicized through mass media. The phone calls are attended and complaints are recorded by the operators on the software and an automatic grievance number is generated which can be used for tracking of the complaint on the website. Jan Suvidha Kendra is active 24x7, earlier the timings for registering complaints was limited to the office timings, but now they are just a phone call away to register their complaint at any time of the day. Moreover, people are not required to visit government offices again and again for filing of grievances. Just after registering of grievance two SMS are sent. The first SMS is sent to the complainant, informing the name and department of the official who will examine the complaint. The second SMS is sent to the officer informing the name of complainant as well as the details of the complaint. Depending upon the criticality and nature of the complaint they are classified into 5 categories. The A category or urgent complaints are to be resolved within 24 hours of filing. The B category complaints are to be resolved within 72 hours of the filing while the C category complaints need to be addressed within 7 days of filing. A fourth category of complaint logs in the allegations against any government official and the fifth category records complaints against public representatives. The fourth and fifth categories of complaints are required to be registered with an affidavit and have to undergo specific legal procedures. Since its launch in May 2012, about 1885 complaints have been recorded; the redressal rate is about 74.16 percent, while 7 percent complaints are pending. Currently 18.83 percent complaints are defaults. However, the administration if working hrd to reduce both the pendency and defaults.




 Subscribe
Subscribe
 Flipbook
Flipbook PDF (5.0 MB)
PDF (5.0 MB)


