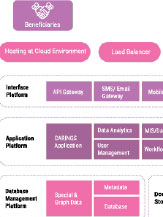
Multi-Factor Authentication (MFA) for machine identities adds an extra layer of security by requiring multiple verification methods during authentication. This helps protect against cyber threats by ensuring that only authorized machines can access systems and data. Implementing MFA for machine identities reduces the risk of unauthorized access and strengthens network security.
In today’s digital age, industries across various sectors are transitioning to digital channels at an unprecedented pace. This shift has led to a significant increase in the number of machine identities, which include mobile devices, Internet of Things (IoT) devices, virtual machines, containers, and APIs. As organizations migrate to cloud environments and adopt perimeterless networks, securing these machine identities becomes crucial to prevent data breaches and unauthorized network access.
Cybercriminals employ sophisticated techniques such as malware, ransomware, and man-in-the-middle (MITM) attacks to compromise organizational security. Robust authentication mechanisms are essential to verify the identities of both users and machines. MultiFactor Authentication (MFA) emerges as a core component of Identity and Access Management (IAM), providing additional verification layers to minimize the risk of security breaches. By requiring multiple forms of evidence to prove identity, MFA significantly enhances the security of machine identities in a complex, perimeterless network landscape.
Importance of Securing Machine Identities
Machine identities are digital credentials used by machines to authenticate and communicate securely with other machines, services, and applications. These identities are essential for establishing trust and ensuring secure interactions in digital ecosystems. As the number of connected devices and applications grows, the potential attack surface for cyber threats expands. Unsecured machine identities can be exploited by attackers to gain unauthorized access, disrupt services, and steal sensitive data. A single compromised machine identity can lead to a cascade of security incidents, undermining the integrity of an entire network. For example, attackers can use stolen machine identities to move laterally within a network, bypassing traditional security controls and escalating privileges. This makes securing machine identities a critical priority for organizations seeking to protect their digital assets and maintain operational continuity
Role of MFA in Safeguarding Machine Identities
MFA enhances security by requiring two or more of the following factors to verify a user’s identity:
Knowledge factor: Something the user knows, such as a PIN or password.
Possession factor: Something the user has, like an encrypted security key or a time-based onetime password (TOTP).
Inherence factor: Something specific to the user, such as a fingerprint or facial scan. By leveraging these diverse factors, MFA provides a robust defense against attacks that might exploit a single point of failure, such as a stolen password or compromised device
Achieving a Zero Trust Security
Implementing MFA is a cornerstone in achieving a Zero Trust security model. Zero Trust operates on the principle that no entity—inside or outside the network—should be trusted by default. Instead, every access request must be continuously verified, ensuring that only authenticated and authorized entities are granted access. MFA supports this model by:
- Validating Every Access Attempt: Each access request is subject to rigorous verification, regardless of its origin. This approach effectively reduces the risk of lateral movement by attackers within the network.
- Enhancing Visibility and Control: MFA provides detailed logs and analytics on access attempts, allowing security teams to monitor and respond to suspicious activities in real-time.
- Strengthening Endpoint Security: By requiring multiple authentication factors, MFA reduces the risk of compromised endpoints, ensuring that only legitimate devices can communicate within the network.
Key Components
Knowledge Factor
It involves information that only the user knows, such as a password, PIN, or answer to a security question. This factor is the most traditional form of authentication. Despite its common use, it has vulnerabilities, primarily because it relies on the secrecy of the information. If the knowledge factor is compromised, for instance, through phishing or data breaches, unauthorized users can gain access. However, when combined with other MFA factors, the security is significantly enhanced.
Possession Factor
It requires the user to have a physical item to verify their identity. Common examples include:
- Security Tokens: Devices that generate a time-sensitive code.
- Smart Cards: Cards that contain encrypted authentication information.
- Mobile Devices: Smartphones that receive SMS or app-based OTPs. These methods ensure that the user has a specific item in their possession at the time of authentication. While more secure than relying on knowledge factors alone, possession factors can be susceptible to theft. For e.g., if a mobile device is stolen, thief may be able to intercept OTPs unless additional measures are in place.
Inherence Factor
It is based on biometric data, which is unique to the individual, including:
- Fingerprint Scans: Using the unique patterns of an individual’s fingerprints.
- Facial Recognition: Identifying a user based on their facial features.
- Iris Scans: Analyzing the unique patterns in the colored part of the eye.
- Voice Recognition: Verifying identity through unique voice patterns. Biometric authentication is highly secure because it is extremely difficult to replicate someone’s inherent characteristics. However, technology requires proper implementation to avoid issues like false rejections or spoofing.
Benefits
Strong User Authentication
Cyberattacks often exploit stolen credentials. By mandating MFA, organizations ensure users verify their identities through multiple methods, reducing the potential risk. Even if a password is compromised, additional verification steps provide a strong defense, significantly enhancing the protection of sensitive data and resources.
Compliance with Industry Regulations
MFA is crucial for compliance with industry regulations. In the financial sector, it supports compliance with Payment Card Industry Data Security Standard (PCI-DSS) and Service Organization Control regulations. In healthcare, MFA helps meet Health Insurance Portability and Accountability Act (HIPAA) requirements, securing patient information and enhancing data security.
Scalability for Evolving Workforce
As hybrid work models and cloud transitions become prevalent, MFA helps manage and monitor complex access requests. Adaptive MFA assesses the risk of user requests based on factors like device and location, enabling dynamic policy adjustments and step-up authentication. For highly sensitive information, additional verification steps, such as biometric scans or codes sent to phones, may be required.
Compatibility with Single Sign-On
Integrating MFA with Single Sign-On (SSO) allows seamless user authentication without compromising productivity. Users benefit from not having to remember multiple passwords, while secondary MFA ensures secure access. This integration simplifies the user experience while maintaining high security standards.
Effective MFA for the Cloud
In cloud security, Federated Identity Management (FIM) plays a pivotal role by establishing secure connections between webbased applications and identity providers using Public Key Infrastructure (PKI). FIM facilitates trusted relationships between organizations and third parties, enabling secure sharing of digital identities across multiple domains.
PKI Security
The importance of MFA in cybersecurity was underscored by the Colonial Pipeline hack. PKI is one of the most common MFA forms, providing certificate-based identity authentication with a high level of assurance. PKI supports robust certificate-based security, enhancing network efficiency and security.
Addressing the Downsides
While MFA offers robust security benefits, it also comes with several challenges, such as increased complexity, costs, and potential user resistance. Organizations must weigh these factors carefully and implement strategies to mitigate the negative impacts, such as providing comprehensive user training, ensuring reliable infrastructure, and planning for ongoing support and maintenance.
Implementation
Planning and Strategy
Before implementing MFA, organizations need to conduct a thorough assessment of their current security posture and identify areas where machine identities are most vulnerable. This involves:
- Determine which systems, applications, and devices require the highest levels of protection.
- Evaluate the potential risks and threats to these assets, considering factors such as access patterns, user behavior and data sensitivity.
- Develop comprehensive security policies that define how MFA will be implemented, including which factors will be used and under what circumstances.
Technology Selection
Choosing the right MFA technologies is crucial for effective implementation. Organizations should consider:
- Compatibility: Ensure that MFA solutions are compatible with existing systems.
- Scalability: Select technologies that can scale with the organization’s evolving needs.
- User Experience: Opt for solutions that provide a seamless and user-friendly authentication process to minimize resistance and encourage adoption.
Deployment and Integration
Deploying MFA involves integrating it with the organization’s IAM infrastructure and ensuring that it is seamlessly incorporated into daily operations. Key steps include:
- Implement MFA alongside SSO solutions to streamline the authentication process and enhance security.
- Leverage FIM to facilitate trusted interactions between different domains and services.
- Use PKI for robust certificate-based authentication, ensuring that digital identities are verified.
User Training and Support
Successful MFA implementation requires comprehensive user training and ongoing support. This involves:
- Training Programs: Develop and deliver training programs to educate users about the importance of MFA, how it works, and how to use it effectively.
- Support Services: Establish dedicated support services to assist users with MFA-related issues, ensuring that they have access to timely help and resources.
Monitoring and Maintenance
Continuous monitoring and maintenance are essential to ensure the effectiveness of MFA. This includes:
- Conduct regular security audits to identify and address vulnerabilities or gaps.
- Develop and implement incident response plans to quickly address any security incidents.
- Keep MFA technologies and systems up to date with the latest security patches and upgrades.
Conclusion
As digital transformation accelerates, securing machine identities with MFA becomes indispensable. MFA not only strengthens user and machine authentication but also ensures compliance with regulatory standards. By implementing MFA, organizations can protect their digital infrastructure against sophisticated cyber threats and ensure a secure, resilient operational environment.
Contributors / Authors

Savita JainTechnical Director savita@nic.in
- Tag:
- Internet
- Technology
- eGov
- Tech
Savita Jain
Technical Director
NIC HQ, Cyber Security Team
A-Block, CGO Complex, Lodhi Road, New Delhi - 110003